Cyber Espionage, Data Breaches, and Malware: Inside the World of Chinese APT Threats

Table of contents
Rather than a one-off cyberattack, Advanced Persistent Threats (APTs) are calculated, long-term campaigns. APTs aim to infiltrate critical infrastructure and steal valuable data, and they are a favored tactic of the Chinese government.
But what exactly are Chinese APT threats? And why should you, as a CISO or information security officer, be concerned? Let’s break this down, and find out how to combat this rising cybersecurity threat.
What are Chinese APT threats?
Advanced Persistent Threats (APTs) are cyberattacks designed to gain unauthorized access to systems and remain undetected for extended periods.
Unlike opportunistic attacks, APTs involve significant planning, resources, and persistence.
APT goals include:
- Cyberespionage: Enabling the surveillance and disruption of critical infrastructure and government operations worldwide.
- Data theft: Including intellectual property, trade secrets, or valuable government information.
Chinese APTs are often state-sponsored, giving them access to advanced tools and substantial funding.
Chinese hacking groups are known for their focus on strategic industries, such as:
- Defense: To disrupt military operations and supply chains.
- Finance: To destabilise national economies.
- Technology: To hinder or steal technological developments.
- Telecommunications companies: To block communication or spread disinformation.
- Healthcare: To expose and exploit public health records on a large scale.
If your organization operates in any of these sectors, then understanding the tactics of Chinese APTs is critical. Let’s identify the main Chinese APT groups at large, along with current trends and case studies to be aware of.
Chinese APT hacking groups
There are many Chinese hackers and groups, but here are some of the main APT organizations to know.
- APT1 (Comment Crew/ PLA Unit 61398): One of the earliest identified Chinese APT groups, APT1 is infamous for targeting American private sector organizations for cyber espionage.
- APT10 (Stone Panda): Known since 2009, APT10 has been linked to campaigns that target government operations, military operations, and business across multiple industries.
- APT41 (Winnti Group): A group that combines state-sponsored espionage with financially motivated cybercrime. Their members are listed on the FBI’s Most Wanted page.
- APT27 (Emissary Panda): Focused on sectors such as government, aerospace, manufacturing, betting, and defense, APT27 often exploits remote access vulnerabilities to infiltrate systems.
- Salt Typhoon: Named after a moniker by Microsoft and active since 2020, Salt Typhoon is famous for allegedly breaching US Internet service provider networks and wiretap systems, including Lumen Technologies, Verizon, and AT&T.
Chinese hacking trends
Chinese APTs are evolving. While earlier campaigns were bold and large-scale, recent operations have become more covert and sophisticated. Here are some trends to watch.
1. Using ransomware to mask cyber espionage
Some APT hacking operations can conceal their workings behind malware and seemingly “one-off” ransomware attacks.
Several intrusions have been analyzed in recent years and revealed to be more than just a ransomware attack, but rather a more sophisticated cyberespionage effort.
Using ransomware gives governments—like the People’s Republic of China—an excuse to claim they weren’t responsible, hide their true motives, and provide the threat actors with a financial reward for their services.

2. Operating via private companies
Chinese cyber operations often rely on private service providers.
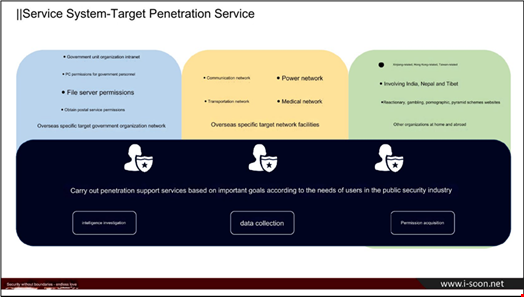
In February 2024, a leak on GitHub exposed internal documents belonging to iSoon, a Shanghai-based company that supports hacking operations on behalf of Beijing.
It advertises an “APT service system”, “target penetration services”, and “battle support services.”
Infosecurity Magazine posted presentation slides from the group, including this hacking campaign against the Indian and Nepalese governments.
3. Merging cyberattack methods
In 2024, Chinese threat groups have been observed blending different attack methods to increase their impact.
For example, in an attack that affected India, Taiwan, Australia, the US, and Hong Kong, a group called Evasive Panda used:
- Watering-hole cyberattacks: This involves compromising a popular website to allow the distribution of malware.
- Supply chain cyberattacks: By infiltrating third-party vendors or software providers, attackers gain indirect access to their primary targets.
The attackers took over a Tibetan Buddhism website, a Tibetan language translation site, and a Tibetan news site, which then hosted malware.
Experts said, “It is impossible to know exactly what information they are after… [but] the victim’s machine is like an open book. The attacker can access any information they want.”

A high-profile case study: China hacking US telecoms
Let’s look at a real-life example of Chinese APT activity to understand the scope and impact of their operations.
At least 8 US telecom providers were allegedly hacked by the Chinese group, Salt Typhoon. Several large organizations were affected, including the FBI, Verizon, AT&T, and Lumen Technologies, and over a million people’s metadata was hacked.
And the consequences reached all the way to the White House.
Media reports stated that the hackers were targeting call records of senior politicians and US officials, including Donald Trump, Kamala Harris, JD Vance, and members of the Biden administration.
The Chinese Embassy in Washington denied the claims and stated that China opposed “cyber thefts in all forms,” according to Reuters.
However, Anne Neuberger, the Deputy National Security Advisor for Cyber and Emerging Technology stated, “Right now, we do not believe any have fully removed the Chinese actors from these networks … so there is a risk of ongoing compromises to communications.”
Even worse, despite being ‘one of the largest intelligence compromises in US history’, NBC News reported that most victims had not been notified of the breach.
Takeaways
So, what can we learn about APT groups from the alleged Salt Typhoon attack?
- Political disruption: APT groups can use leaked data to disrupt, confuse, or undermine democratic processes in other countries—such as in this instance, during the US election.
- Reporting shortcomings: Hacked organizations are not always informing their victims of data breaches.
- Ongoing damage: APT cyberattacks can remain lodged in online systems for some time, continuing to exploit and extract sensitive data.
Law enforcement response to APTs
This year, FBI director Christopher Wray mentioned that nations like China are increasingly relying on “cyber operations” to undermine the US government.
Across the world, governments and law enforcement agencies are taking action against Chinese APTs, but the challenges are immense:
- Indictments and sanctions: The US Department of Justice has indicted members of Chinese APT groups for cyberespionage, and sanctions have been imposed on entities supporting such activities.
- Cybersecurity regulators: For example, the Cybersecurity and Infrastructure Security Agency (CISA) exists to regulate and enforce cybersecurity measures in the US.
- International collaboration: Organizations like NATO and the Five Eyes intelligence alliance are working together to share intelligence and improve defenses against cyber threats.
- Cybersecurity advisories: The US National Security Agency recently partnered with other agencies to publish a paper on cyber activities associated with the threat actor APT40.
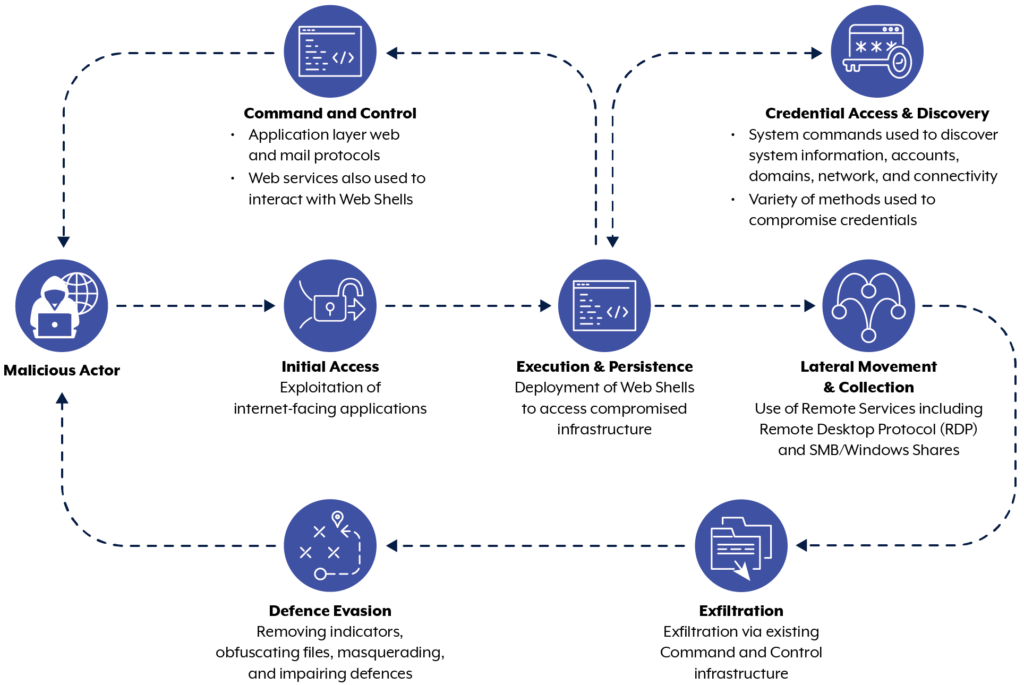
However, pinpointing the exact source of all attacks is difficult due to the anonymity of cyber operations and the use of proxy networks. This means that private organizations must take proactive measures to protect themselves, too.
How can you protect your organization from APT threats?
Defending against APTs requires a multi-layered approach.
Here are actionable steps to enhance your organization’s security:
- Conduct regular vulnerability assessments: Regularly test your systems to identify and patch vulnerabilities before attackers can exploit them.
- Educate your team: Train employees to recognize phishing attempts and other social engineering tactics used by APT groups, and to follow data protection protocols.
- Monitor your supply chain: Vet third-party vendors and implement security protocols to reduce the risk of supply chain attacks.
- Invest in threat intelligence: Use services that provide real-time data on potential threats targeting your industry.
This is where CybelAngel’s External Attack Surface Management (EASM) can make a difference.
CybelAngel’s EASM solutions help organizations identify vulnerabilities, monitor their external attack surfaces, and stay ahead of threats.
In particular, it operates via:
- Asset discovery and monitoring: Identifying vulnerable digital assets, before hackers do.
- Data breach prevention: Safeguarding confidential data and avoiding exploitation.
- Account takeover prevention: Preventing the sale of stolen credentials on the dark web.
- Dark web monitoring: Tracking cybercriminal conversations and forums to sidestep potential attacks.
- Brand protection: Removing fake accounts and malicious domains associated with your organization.
Conclusion
The threat of Chinese APTs is real and growing, from intellectual property theft to critical infrastructure attacks, and politically-motivated disruptions.
By understanding the methods and goals of these groups, you can better prepare your organization to defend against them.
You can also schedule a demo of CybelAngel’s EASM service today and see how it can protect your organization against even the most sophisticated APT threats.

