Your Guide to the Threat Intelligence Revolution

Table of contents
CybelAngel has evolved. What began as external attack surface management (EASM) has become something broader: external threat intelligence (ETI).
This shift isn’t just about rebranding. It’s about harnessing tactical threat intelligence to find out who’s behind the biggest cybersecurity risks, and how to stop them in their tracks.
Let’s break down what external threat intelligence means, cyber threat landscape trends in 2025, and the best ETI practices and tools to counteract them.
1. What is external threat intelligence?
External threat intelligence (ETI) focuses on cybersecurity threats before they cross into your network, and delivers data on the threat actors behind them.
ETI reviews your exposed assets and adds the missing layer: adversary intent. It monitors the digital spaces where attackers operate, such as Telegram channels and dark web forums.
For example, ETI might track:
- Phishing kits targeting your customers, and who is behind them.
- Criminals listing stolen credentials for sale on Telegram.
- Lookalike domains registered by new threat actors.
These aren’t internal events. They’re external precursors. And they’re often the earliest signals of an incoming attack.
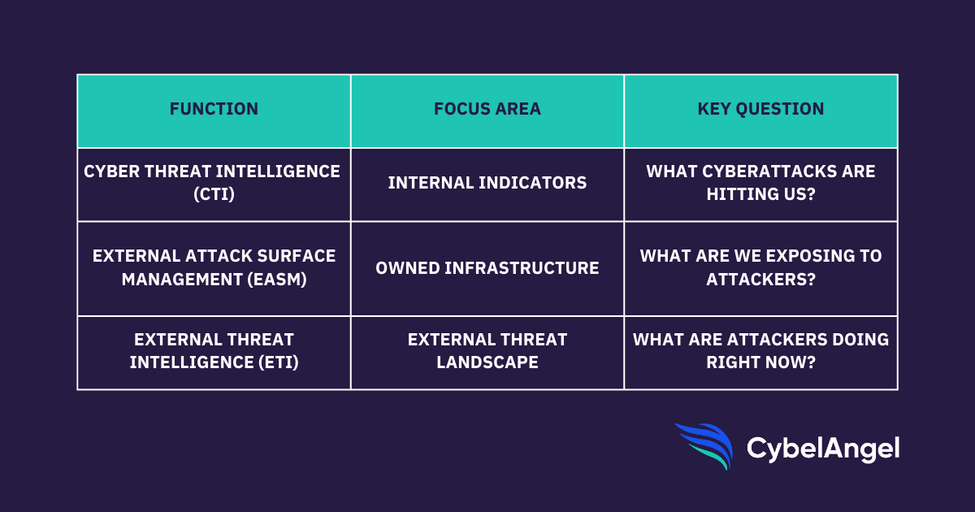
What’s the difference between, CTI, EASM, and ETI?
There are several different types of threat intelligence feeds.
Here’s how they differ.
- Cyber threat intelligence (CTI) has traditionally focused on known indicators of compromise (IOCs), such as IP addresses, malware hashes, and domain names. It’s useful for identifying threats that have already been seen in the wild. But CTI often tells you what happened, not what’s coming.
- External attack surface management (EASM) builds on that by mapping your internet-facing assets. It shows you what you’ve exposed, such as unpatched servers, forgotten subdomains, and misconfigured cloud drives. EASM asks, “What vulnerabilities do I have out there that could be attacked?”
- External threat intelligence (ETI) goes further, with insight into the people behind the threats. ETI identifies who’s targeting you, how they operate, where they’re coordinating, and what tools they’re using. ETI asks, “Who’s coming after me? How? What’s their intent?”
While CTI tells you what’s dangerous and EASM shows you what’s exposed, ETI connects the two, showing you the people behind the emerging threats.
Here’s a quick summary:
2. How ETI is blocking 2025’s top attack vectors
Let’s break down the top cybercrime methods shaping this year’s threat landscape, and how ETI helps spot them early.
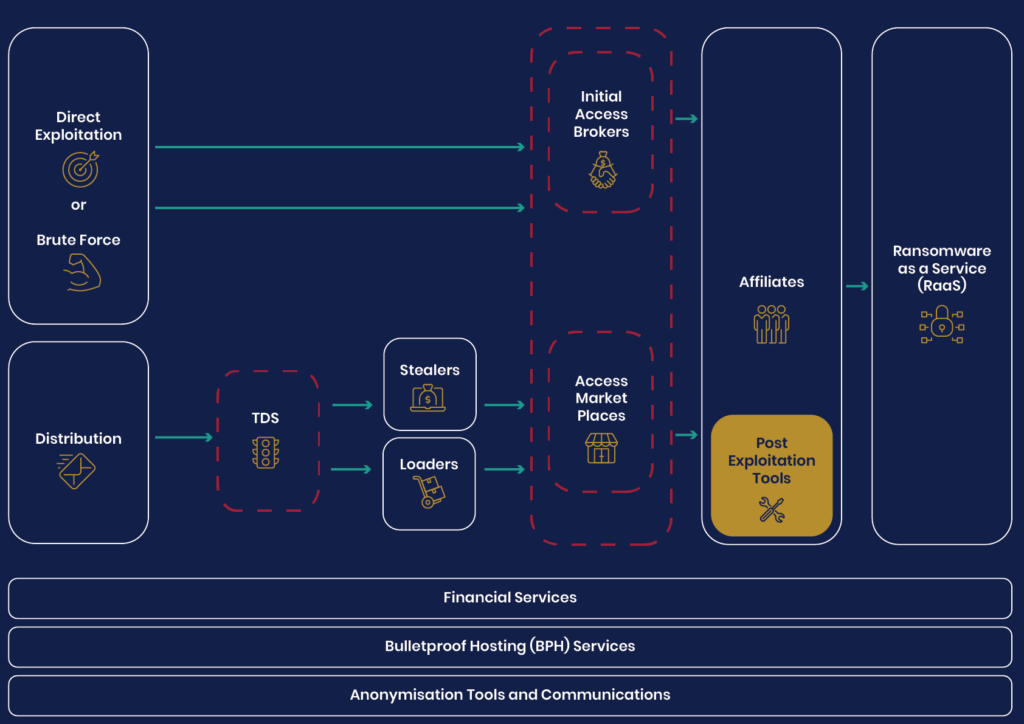
Ransomware-as-a-Service (RaaS)
Ransomware isn’t a single group with a toolkit anymore. It’s a supply chain. CybelAngel’s threat intelligence 2025 report found that ransomware attacks have increased by 42% in the past year, and there’s a 125% increase in active ransomware groups.
Operators now offer plug-and-play ransomware packages, complete with customer support, revenue-sharing models, and ready-made phishing infrastructure.
Take the Lynx ransomware group, for example. After only just emerging in mid-2024, it’s already running a ransomware-as-a-service (RaaS) operation that has hit at least 96 victims.
How ETI helps against RaaS
ETI has a range of ransomware prevention strategies. It offers proactive threat detection to track mentions of your brand, domains, or IP ranges in access broker forums and Telegram groups. It also alerts you when credentials show up in infostealer logs, before they can be used for a ransomware foothold.
X post from CybelAngel about the Akira ransomware gang.
Third-party and supply chain breaches
You might have strong internal security operations. But what about your supply chain vulnerabilities? Attackers are increasingly targeting suppliers and partners, with 91% of organizations experiencing a software supply chain attack in 2024.
For example, the SolarWinds hack in 2020 was recognized as the biggest breach of the century. It happened when threat actors inflitrated an IT monitoring platform, which delivered malware to 30,000 companies and governing bodies.
How ETI helps against supply chain breaches
ETI monitors threat actor interest in vendors, cloud providers, and managed services you rely on. It tracks dark web discussions, exploit trades, and even shared TTPs across campaigns. This means you can proactively engage with your vendors’ security teams when you see the signs.
X post from CybelAngel about supply chain threats.
AI-powered phishing and deepfakes
Phishing is getting harder to spot. Thanks to generative AI phishing, attackers now create flawless emails, clone executive voices, and generate real-time video deepfakes. CybelAngel’s report found that 67.4% of all phishing attacks used some form of artificial intelligence and machine learning.
In one confirmed case, a Hong Kong company was defrauded after an attacker used deepfake video during a live call, authorizing a fraudulent transaction of $25 million. Human error is a leading cause of cybersecurity breaches, and realistic AI campaigns will only enhance this.
How ETI helps against AI-powered attacks
ETI can identify AI phishing kits circulating in attacker channels. It can also track threat data across campaigns and identify newly created infrastructure, such as phishing sites or hosting services being spun up for impersonation.
X post from CybelAngel about AI phishing campaigns.
Cloud misconfigurations and shadow assets
You can’t secure what you don’t know you own. Shadow IT—unauthorized or forgotten cloud drive risks—is a growing threat. Attackers scan relentlessly for exposed API endpoints, default login portals, and stale DNS records.
For instance, CybelAngel has spotted a 60% increase in exposed digital assets, plus a 20% rise in open and unsecured databases. This can compromise any organization’s security posture and lead to cyber incidents.
How ETI helps against shadow IT
ETI can use threat intel to identify these shadow assets and potential threat indicators. But crucially, it can prioritize them based on threat actor interest. If an attacker is scanning your environment or referencing an asset in a breach forum, ETI helps you spot that signal.
X post from CybelAngel about API threat detection.
Initial access brokers (IABs)
Need access to an executive’s email credentials? You don’t need to breach it yourself. You just buy it.
Initial Access Brokers (IABs) sell credentials, session cookies, and device fingerprints daily across encrypted Telegram channels and closed forums. Once access is sold, ransomware affiliates or phishing crews step in.
According to The Hacker News, IABs are shifting tactics and selling more credentials for less, increasing their impact across the board.
How ETI helps against IABs
ETI can monitor IAB marketplaces and dark web chatter, alerting you when your domains or IPs appear (before that access is used in an attack). This can disrupt the whole ransomware ecosystem and block criminals from taking advantage.
3. Threat intelligence frameworks to follow
Raw intelligence, such as IP lists, forum screenshots, and phishing domains, doesn’t mean much on its own. You need structure. And that’s where frameworks come in. They provide a system for understanding risk, responding faster, and showing impact.
MITRE ATT&CK
MITRE ATT&CK is the gold standard of cybersecurity. ATT&CK maps threat information across tactics (like initial access or privilege escalation) and techniques (like phishing or credential dumping).
It helps teams track how attackers move through environments, and spot patterns across incidents.
For instance, you could map your ETI data with ATT&CK to find out not just what’s happening, but what might happen next.
How MITRE ATT&CK works by Gary Ruddell. Source.
MITRE D3FEND
Where ATT&CK maps how attackers operate, D3FEND maps the defensive countermeasures.
Developed by MITRE as well, D3FEND helps security teams link detections to concrete technical controls. This gives security professionals the best methods and workflows to defend against incoming threats.
ETI data can be used to inform this strategy, assisting in vulnerability management and providing strategic threat intelligence.
A preview of the MITRE D3FEND page. Source.
The Diamond Model
The Diamond Model of Intrusion helps threat intelligence services to understand risks via four key elements:
- Adversary: The group or stakeholders responsible for the cyber incident.
- Infrastructure: The assets that the adversary exploits during the attack (e.g. servers, domains).
- Capability: The method, tool, or technique used by the adversary during the attack (e.g. malware, deepfakes).
- Victim: The person or organization being targeted by the attack.
This model can be helpful for external threat intelligence teams, as it gives visibility into attacker infrastructure and intent.
STIX & TAXII
These are data formats and transport protocols, not threat models. But they’re still essential for automation between security tools .
- STIX describes the cyber threat information (including motivations, abilities, capabilities, and response).
- TAXII helps move it between tools.
Together, these methods can help you to channel ETI data into your network. This lets you enrich security alerts and correlate external threats with internal signals, all at machine speed.
4. How to build an intelligence-led security team
External threat intelligence is only useful if it drives action. That means integrating it, not just collecting it. If you want to be proactive instead of reactive, then you need a program that makes external threat intelligence part of your decision-making.
Here’s how to make it happen.
- Embed intelligence across functions: Threat intel isn’t just for the security team. It should feed your incident response maps, risk management workflows, executive reporting, and beyond.
- Track the right metrics: Link your threat analysis to essential cybersecurity metrics, such as the time to detect emerging threats, time spent on false positives, and threats identified before exploitation.
- Make it real-time: The biggest value of ETI is speed. You’re not waiting for threat reports that land two weeks after the attack. You should be ahead of the game and ready to act fast.
- Mature your capabilities over time: You don’t need to solve everything at once. Start with foundational coverage, such as brand protection, dark web alerts, and credential leaks. Then layer in enrichment, automation, and actor tracking.
5. AI: The future of external threat intelligence
What will threat intelligence look like in the next few years? Ultimately, artificial intelligence is going to change the face of threat intelligence forever. AI is now part of the attacker’s toolkit, as well as the defender’s.
In 2025, we’re seeing both sides move faster because of it. But here’s the difference: attackers don’t need AI to be perfect. They just need it to be ‘good enough’ to trick a human or bypass a control.
AI-powered threat detection—and cybercrime—are the future.
Let’s explore both sides.
How attackers are using AI
As we’ve already discussed, artificial intelligence is opening up multiple new workflows for hackers. Here are some quick examples.
- Phishing at scale: AI can generate tailored phishing emails that mimic tone, style, and even internal jargon. It’s fast, cheap, and far harder to spot than last year’s generic lures.
- Voice and video deepfakes: Deepfake audio is now part of high-value BEC kits. Some even come bundled with scripts and real-time tools that clone executive voices to approve wire transfers over a call.
- Automated reconnaissance: GPT-powered scrapers can scan company sites, LinkedIn profiles, and more to get to know their targets in preparation for cyberattacks.
How defenders are using AI
Cybersecurity professionals are also making use of AI, and it could make all the difference to their threat intelligence feeds this year.
- Signal over noise: Threat teams are flooded with data. AI helps by clustering IOC feeds, summarizing chatter across forums, and surfacing what’s actually new or relevant. Not every domain is a threat, and AI helps decide which ones matter.
- Faster triage: When ETI platforms flag suspicious activity, AI can enrich that data in real time, pulling in reputation scores, historical context, and actor links. That means less time digging, more time acting.
- Predictive prioritization: AI models can spot campaign patterns—“this infrastructure looks like it’s part of X group’s operations”—and flag likely next steps.
6. CybelAngel: An external threat intelligence platform
CybelAngel has recently evolved from an EASM platform into an ETI tool. It uses threat hunting technology, darknet monitoring tools and more to give you an overview of your risks, and the people behind them.
While CybelAngel previously offered a map of your external assets, it can now also tell you who is plotting a route across that map.
That difference matters.
Because the earlier you spot intent, the more options you have.
For example, you can take down a domain before it’s weaponized. Rotate credentials before they’re sold on the dark web. Or warn third parties before security incident grows.
Closing thoughts
External threat intelligence helps you act before hackers do. You can spot adversary intent, prioritize the right risks, and act while there’s still time to prevent impact.
At CybelAngel, we’re building ETI to give you that edge.
Reach out for a demo to see it in action, and you’ll be one step closer to being proactive, rather than reactive.

