All About EASM [Securing Your Attack Surface]

Table of contents
Quick test: Can you think of every Internet-facing asset that your organization owns? If you’re struggling, you’re not alone. While the average organization has 4000 visible digital assets, many companies find it difficult to track them all. And cybercriminals are all-too-happy to take advantage of this.
External attack surface management (EASM) is designed to help you secure the unknown assets and overlooked vulnerabilities in your organization’s digital perimeter—before they become potential threats. Let’s explore EASM in depth, and run through some tips to implement it effectively.
1. What is EASM?
Your external attack surface refers to every public-facing digital asset that your organization owns. This includes (but is not limited to):
- Websites
- API security
- Cloud services
- Forgotten test environments
When left unmanaged, these apps and assets can easily be exploited by hackers, cybercriminals, or state-sponsored threat actors.
External attack surface management (EASM) is all about identifying, tracking, and managing these digital assets to reduce the risk of cyberattacks.
Think of it like managing a building’s security. It’s about identifying all the doorways and entry points, then ensuring that they’re locked, with only authorized people having the keys.
While other cybersecurity tactics are more “reactive” to cyber threats, EASM is a proactive approach that tackles potential vulnerabilities before they become an issue.

2. Why is the External Attack Surface expanding?
External attack surface risk management is a hot topic, with a Gartner report anticipating it will become a rising security feature in the coming years.
Here are 6 reasons for this:
- The COVID-19 pandemic: The world underwent a rapid period of digital transformation during the pandemic. Whereas previously, EASM growth was slow and predictable, it’s now exploded into a complicated network of digital assets and attack vectors that are difficult to secure. And they’re constantly evolving.
- Cloud security: Many businesses, governments, public and SaaS organizations have migrated their workflows to the cloud, which can reduce visibility of their cyber assets and pose risks via the third-party applications they use. In its 2024 report, CybelAngel reported an 11% increase in exposed cloud data year over year.
- Remote work: Your external attack surface isn’t just your own anymore. The rise of remote work has introduced a host of new endpoints, IP addresses, web applications, VPNs, and cloud collaboration tools that expand the attack surface.
- Shadow IT: Employees may deploy unauthorized applications or services, creating assets that go untracked by security teams. Their threats become your threats, and it can easily turn into a vast spiderweb of security risks.
- IoT devices: Connected devices are often overlooked in security plans, even though they’re increasingly targeted by attackers.
- Supply chain vulnerabilities: Every organization has an entire ecosystem of providers, distributors, partners and vendors who, in turn, bring along their own supply chains. These always have their own vulnerabilities, along with varying levels of maturity in cybersecurity practices.
So, who does this affect?
In short, everyone.
Simply carrying out routine business with other companies will increase risks in your own systems and processes. And employing even one person can lead to exposed assets and new vulnerabilities.
3. EASM vs. ASM and other cybersecurity workflows
EASM is often confused with other cybersecurity practices like Attack Surface Management (ASM), vulnerability management, and penetration testing. Here’s how they differ:
- ASM (Attack Surface Management/ Attack Surface Monitoring): While ASM encompasses the full attack surface (both internal and external), EASM focuses exclusively on internet-facing assets. EASM can be seen as a specialized subset of ASM.
- Vulnerability management: A vulnerability assessment can identify and remediate weaknesses in known assets, but it doesn’t always address unknown or unmanaged assets.
- Penetration testing: Pen tests are periodic and manual, while EASM operates continuously, offering ongoing protection.
- Threat intelligence: While threat intelligence focuses on external threats, EASM ties those threats directly to your exposed assets, making it more actionable.
Organizations can combine EASM with other security measures to have the most holistic cybersecurity strategy.
4. The 4 benefits of EASM cybersecurity
Implementing EASM delivers several key advantages:
- Improved visibility: EASM ensures that all external-facing assets—even shadow IT and forgotten endpoints—are accounted for. This is essential for preventing blind spots in your security strategy.
- Proactive risk management: By identifying and prioritizing vulnerabilities with a comprehensive risk assessment, EASM helps you address online threats before attackers spot them.
- Regulatory compliance: Maintaining an inventory of external assets and entry points and securing them can help meet compliance requirements for GDPR, HIPAA, and other regulations.
- Enhanced incident response: When incidents occur, having a comprehensive map of your attack surface allows for faster containment and resolution.
For example, a company using EASM could discover an outdated application still exposed to the internet. Addressing this vulnerability proactively could prevent a costly data breach.
5. The 3 challenges of EASM solutions
Despite its benefits, EASM isn’t without challenges. Here are some common hurdles that organizations face:
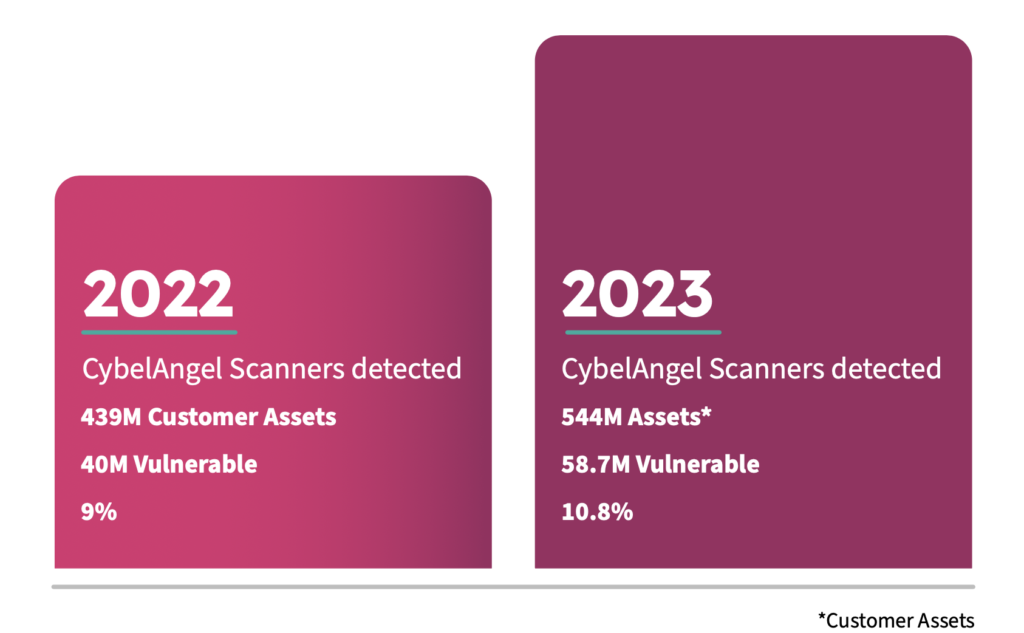
- Asset discovery: In sprawling IT environments, finding every internet-facing asset can feel like searching for a needle in a haystack. CybelAngel’s 2024 ‘State of EASM’ report found 7.6k exposed and compromised credentials each month.
- Continuous monitoring: The dynamic nature of digital ecosystems requires constant vigilance, which can strain resources.
- Risk prioritization: Not all vulnerabilities are created equal. Determining which issues to address first is critical but challenging.
To overcome these challenges, organizations should look for EASM solutions that offer automation, integration with existing tools, and robust reporting features.
6. Use cases: 3 EASM stories
Let’s look at some real-life examples of how external attack surface management can safeguard companies.
Preventing data breaches
Lagardère is an international group with operations in more than 40 countries. But with its growth, it also faced an increase in its external attack surface.
With an increasingly complex digital ecosystem, they utilized CybelAngel’s EASM software to prevent over 200 third-party data breaches per year.
They also implemented a faster incident response time, using real-time alerts and incident reports to react quickly.
Safeguarding intellectual property
Signify is a technological business with 38,000 employees and sales of 2.6 billion EUR. Due to its competitive market, any loss of intellectual property could be catastrophic. And with so many employees, there was always a risk of data leaks.
Using CybelAngel’s EASM solution, Signify was able to quickly track and remediate leaks. In the first month alone, they saved millions of dollars’ worth of potential legal actions and privacy violations.
Monitoring supply chains
Sanofi is a healthcare organization with over 100,000 employees in 100+ countries. The pharmaceutical industry is particularly attractive to hackers, meaning that Sanofi needed to take every precaution to safeguard their systems.
Sanofi implemented CybelAngel’s EASM tools to proactively detect and prevent data leaks. It also used it to help their supply chain to improve their own practices, giving each vendor their own ‘maturity map’ to secure their cybersecurity practices.
7. What to look for in an EASM tool
Choosing the right EASM solution can make or break your cybersecurity efforts.
The goal of EASM is to eliminate blind spots and achieve full visibility of all your digital assets through a continuously updated inventory.
Remember, it ensures you know where all your organization’s metaphorical doors are—and that they’re securely locked, with the keys in a safe place.
Here are the features you should prioritize:
- Comprehensive asset discovery: A good EASM solution should continuously monitor and detect exposures and misconfigurations across your entire external attack surface—plus those of your vendors and other subsidiaries.
- High-quality alerts: Look for tools that provide timely, actionable, and prioritized alerts. Alerts should include full contextual detail to help your security team begin remediation efforts immediately.
- Risk management tools: The solution should have features to address key risks, such as credentials leakage, domain squatting threats, and intellectual property exposure. This comprehensive approach prevents multi-vector cyberattacks.
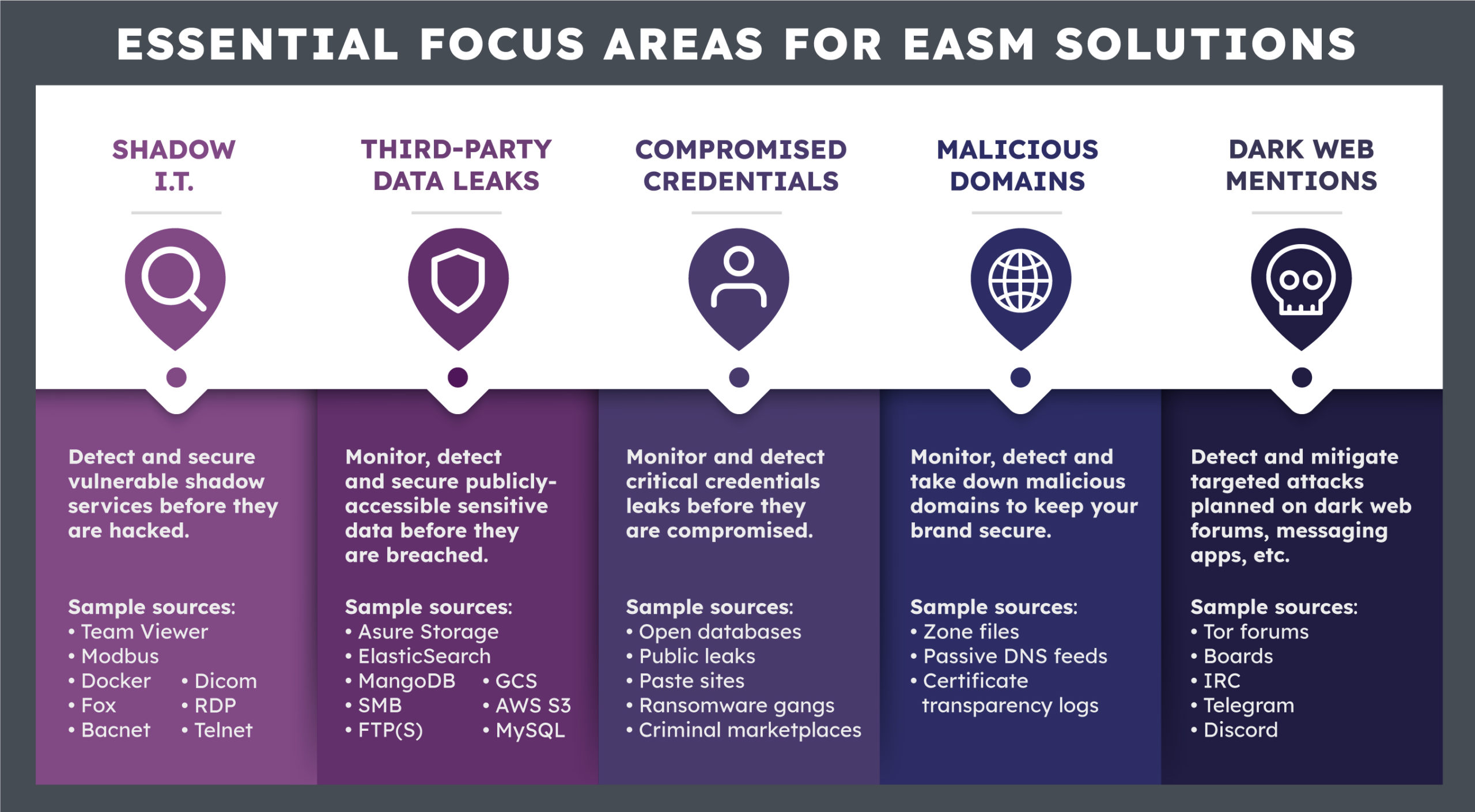
- Key focus areas: Effective EASM tools should monitor and mitigate risks in:
- Vulnerable shadow IT
- Publicly accessible sensitive data
- Critical credential leaks and data breaches
- Malicious domains used for phishing
- Dark web activity
By focusing on these features, you’ll be better equipped to manage your external attack surface effectively and stay ahead of potential threats.
 Your
Your
8. How CybelAngel can support your EASM workflows
With every company having thousands of digital assets, tracking them all can feel overwhelming. But with the right EASM tool, you don’t have to worry.
CybelAngel offers a comprehensive range of external threat intelligence security solutions, including:
- Attack surface management : Spot vulnerable APIs and assets, before cybercriminals see them.
- Data breach prevention: Identify potential data breaches before they happen, and take steps to secure them.
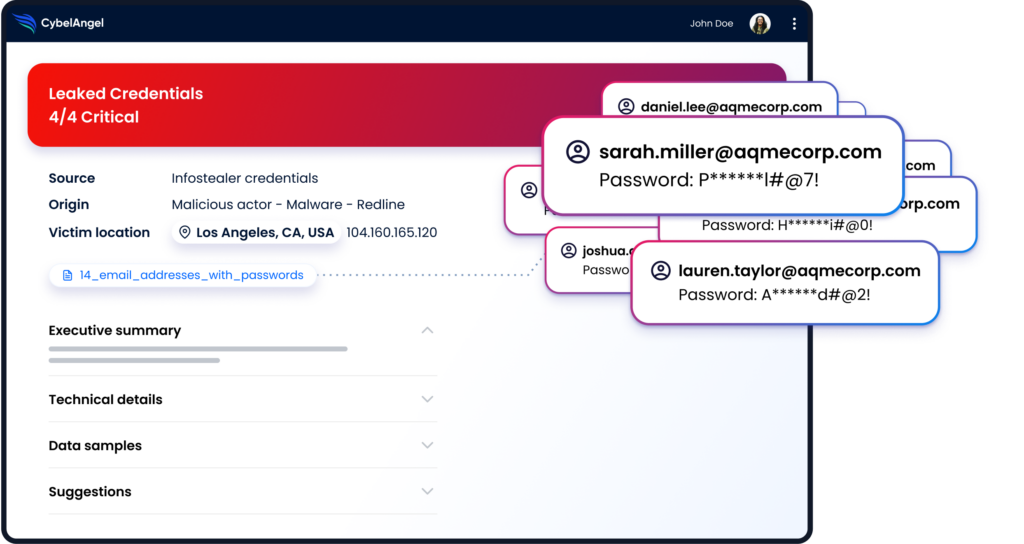
- Credential intelligence: Stop your credentials from being sold on the dark web, and used for phishing or extortion attempts.
- Dark web monitoring: Stay one step ahead of cybercriminals by monitoring their chat forums on the dark web.
- Brand protection: Find and take down malicious domains, fake accounts, and fraudulent apps that might be loaded with malware.
- Remediation services: Reduce your down time by 85% in the event of a ransomware attack, or other form of cyber incident.
- M&A cyber due diligence: Have a review of your cybersecurity posture, and how it could impact valuation and comparisons with other industry players.
- Special threat investigation: Receive support from cyber professionals to quickly identify and resolve any issues.
To learn more, you can always book a demo to learn how CybelAngel’s EASM tools could be tailored to suit your organization’s needs.
9. EASM FAQs
Here are some quick FAQs to help you understand how to safeguard your organization’s attack surface from the outside.
How does EASM differ from traditional vulnerability management?
EASM focuses on discovering and managing external-facing assets, while vulnerability management identifies and fixes weaknesses within known assets. EASM ensures you’re securing everything, even the assets you may not know about.
Do small organizations need EASM, or is it just for enterprises?
EASM is beneficial for organizations of all sizes. Small businesses are often targeted by attackers because their external attack surfaces are less secure. Larger organizations can also be a target due to their extensive asset inventories. EASM provides the visibility and control needed for mitigating this risk.
How often should my attack surface be reviewed?
Continuous monitoring is essential. With new assets constantly being created and existing ones potentially exposed, real-time exposure management is the best way to stay secure.
Can EASM help meet compliance requirements like GDPR or HIPAA?
Yes. EASM provides a comprehensive inventory of external-facing assets, ensuring that sensitive data is secure and compliance standards are met.
Conclusion
The external attack surface is more dynamic and expansive than ever, making traditional security operations insufficient on their own.
At CybelAngel, we understand that managing your entire security posture can feel daunting. But it doesn’t have to be.
With our advanced external threat intelligence solutions, you can take control of your assets and protect your organization from the outside-in. Book a demo to find out more about CybelAngel, and how it could help you to enjoy peace of mind.

