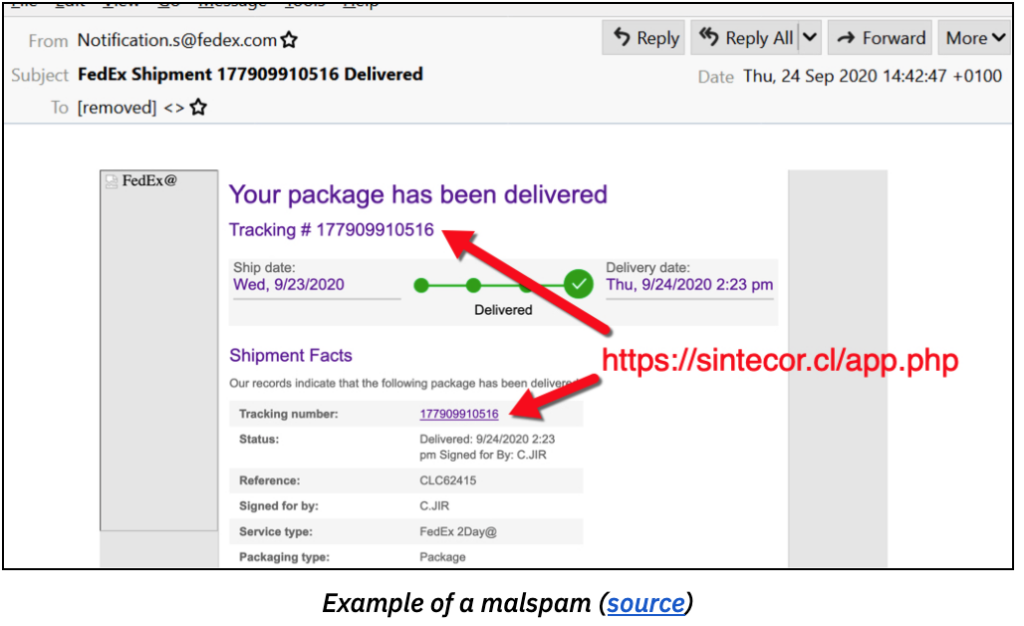
Reconnaissance Phase of the Cyber Kill Chain “Reconnaissance” is the first phase of the 7-step Cyber Kill Chain (CKC) model, which maps sophisticated targeted attacks used by cybercriminals such as Advanced Persistent Threat (APT) actors. In the Reconnaissance phase, an attacker uses different techniques to gather as much information as possible about a target — […]
Are You a Good Ransomware Target?