
Stop Medical Device Leaks
3 min read • January 13, 2021

3 min read • January 13, 2021

3 min read • January 11, 2021

4 min read • January 4, 2021
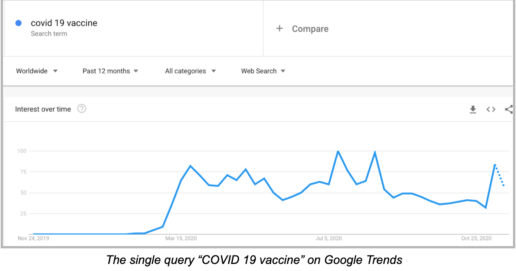
4 min read • December 22, 2020

3 min read • December 12, 2020

3 min read • December 1, 2020