
The Ultimate Compliance Checklist: NIS 2 and DORA Standards
7 min read • April 15, 2025

7 min read • April 15, 2025

3 min read • February 3, 2021

2 min read • February 1, 2021


4 min read • January 24, 2021

3 min read • January 20, 2021

3 min read • January 18, 2021

4 min read • January 15, 2021

3 min read • January 13, 2021

3 min read • January 11, 2021

4 min read • January 4, 2021
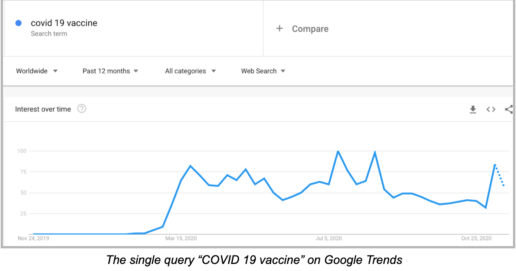
4 min read • December 22, 2020

3 min read • December 14, 2020

3 min read • December 12, 2020

3 min read • December 1, 2020
3 min read • November 18, 2020

4 min read • November 6, 2020

2 min read • November 6, 2020
3 min read • October 28, 2020

3 min read • October 28, 2020

4 min read • October 27, 2020

3 min read • October 21, 2020